As discussed and known very clearly, the ransomware viruses WannaCry si Petya could not cause damage to such a large scale if they did not use a service Windows, left activated by default de Microsoft for at least strange reasons.
SMBv1 is the service that was exploited and could penetrate millions of computers Windows PC from all over the world. Whatever it is Windows 10, Windows 8 or Windows 7, SMBv1 must be deactivated immediately.
Before going into the tutorial, let's see what means this SMBv1.
SMBv1 is the old protocol Server Message Block used by Windows for file sharing in a local network. Later this protocol was replaced by two versions. SMBv2 si SMBv3. The latter can remain active on the system. They are safe and can not be exploited.
According to Microsoft, the SMBv1 protocol has remained active on operating systems for the simple reason that there are a number of old applications using this protocol, they being updated for SMBv2 si SMBv3. Strangely reason to leave something like that in mind knowing beforehand cyber attacks as this protocol is a major risk.
How to disable SMBv1 on Windows 8 and Windows 10
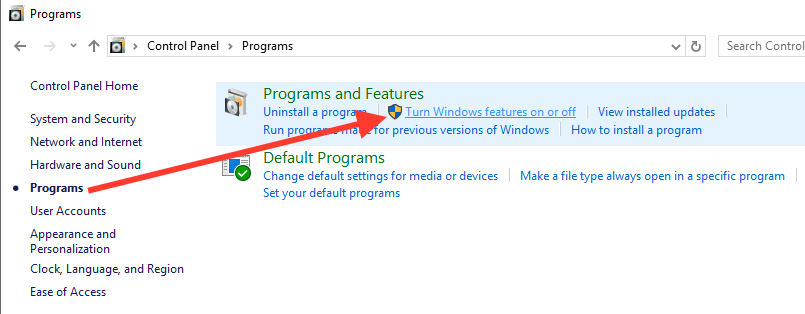
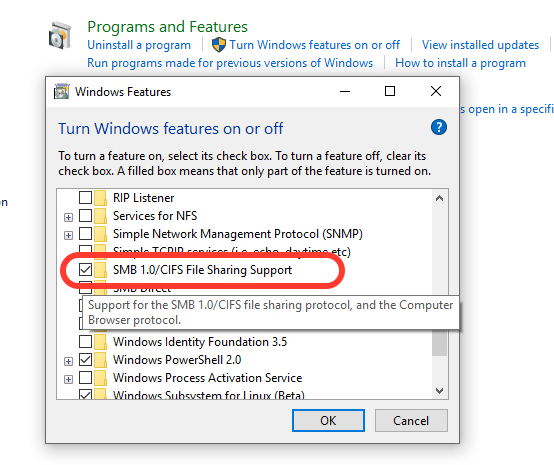
Starting with Windows 10 Fall Creators Update (major update expected in September 2017) Microsoft will disable by default SMBv1. We do not know why so much damage was needed before Microsoft made this decision, but this is another discussion. Until then, SMBv1 can be deactivated very easily from control Panel → Programs → Turn Windows features on or off. You do not need to be expelled in computers to do this.
- Open control Panel and click on "Programs".
- in the list of services, applications and protocols Windows, identify and uncheck "SMB 1.0/CIFS File Sharing Support"
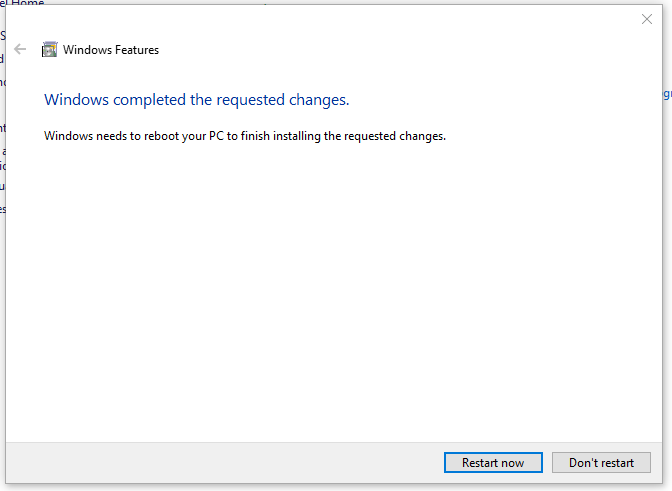
Click "OK", then restart after the deactivation has been successful.
For Windows 7, disabling SMBv1 is a bit more complicated and requires a little attention. You need to edit the registries Windows (Windows Registry) to disable the protocol.
How to disable SMBv1 on Windows 7
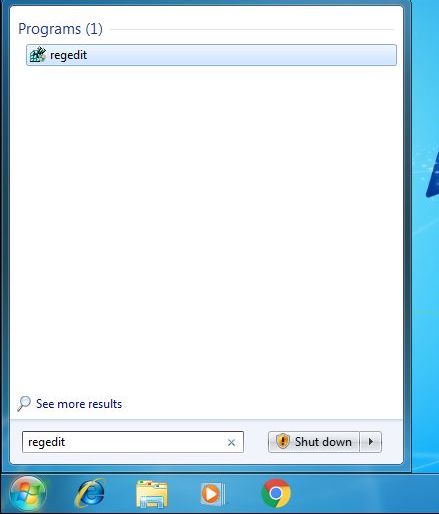
- open the Registry Editor in Strat → search “regedit".
- in Registry Editor we use the bar on the left to navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
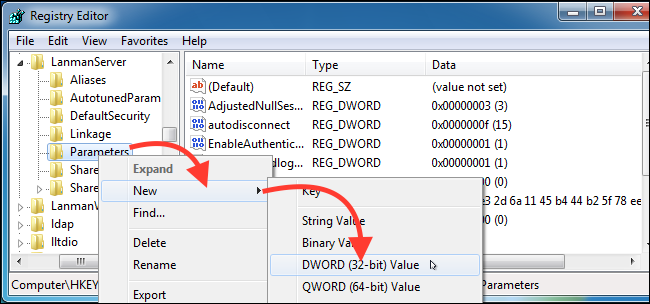
The next step is to create a new one subkey under “Parameters”. Right click on “Parameters”→ New → DWORD (32-bit) Value.
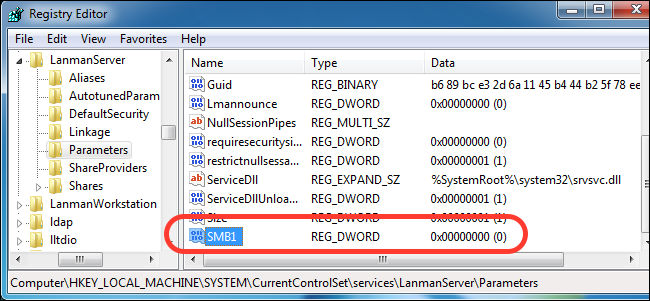
The name of the new value will be "SMB1" with the value "0", which means that it is disabled.
all you have to do now is shut it down registry Editor and restart the operating system. After the restart, the SMBv1 protocol will be disabled.
As a clarification, SMBv1 is not directly responsible for the ransomware infection WannaCry si Petya. Through this protocol, it was only allowed to spread the virus to local networks, infecting millions of computers around the world.
Do not forget to use up-to-date virus software, make backup copies of important files, and last but not least, click on buttons and links you click.